What to Wear for Commencement
Your Commencement ceremony is a momentous occasion, and proper attire is required. This guide will help you understand the dress code, how to wear your academic regalia, and how to collect or return your gown.
Instructions
Commencement is a solemn and august ceremony. All eligible graduands must don the full SMU Academic Regalia in order to walk the stage. The full academic dress consists of a gown, a hood, and a mortarboard (for Bachelor and Master degrees) or tam (for Doctoral degrees). All SMU gowns are designed to be worn closed.
Gown
Put on the gown and fasten using the zipper



Hood
The colours of the hood signify the field of study. Place the hood over your head, with the “V” end of the hood facing front.


Clip the hook of the hood onto the puller of the zipper. Get someone to help you to take the string on the back of the hood and loop it around the button on the opposite end.



Mortarboard
Look for “Front” on the inside of the mortarboard. The mortarboard should fit snugly on your head, and the tassel should be on your right.



Co-curricular Cord
All SMU bachelor’s degree graduands will don the SMU co-curricular cord as part of their graduation academic regalia. The SMU co-curricular cord is draped around the neck with the ends hanging down evenly on either side.
Dress Code
Graduands should wear a collared long-sleeve shirt with a tie, pants, and dress shoes (for men), or a collared long-sleeve shirt or blouse with a skirt or pants and court shoes (for women). They are not allowed to make modifications or alterations to the SMU Academic Regalia, and they are required to uphold the tradition and dignity by following the dress code:
- No display of political, religious*, or personal messages or causes, whether in the form of decorations, badges, scarfs, sashes, pins, or symbols, etc.
*Sikh graduands may wear their turban.
*Female Muslim graduands may wear their hijab/tudung under their gown, hood, and mortarboard/tam. - No accessories that are flashy, distracting, or disrespectful (e.g. sunglasses, headphones, necklaces [over the gown]).
- No adornments that are offensive or not in line with the occasion, such as masks or face paint
- No items that drape over the gown, hood, or mortarboard/tam.
Guests are encouraged to dress in business wear, smart casual attire, or traditional dress. Casual or inappropriate attire such as singlets, shorts, bermudas, slippers, flip-flops, or clothing with offensive words or images should be avoided.
SMU staff on the ground have the right to prevent graduands from participating in the ceremony or walking the stage if they do not comply with the rules or are not suitably attired. SMU staff may exercise due judgment on what dressing is deemed not appropriate. If in doubt, graduands should enquire in advance.


Purchase & Rental
Graduands can choose to purchase or rent the academic gown from our official gown vendor, NW Services Pte Ltd.
Eligible graduands will receive an activation email from NW Services Pte Ltd at your SMU email address. Please click on the link in the email to activate your account. You can only order the gown after your account has been activated. You will be prompted to set a password for your account before proceeding with your order. If you did not receive the activation email, please email admin@nwservices.com.sg to request for the email to be resent to you.
Collection & Return
Gown Collection
Gown collection on campus is by appointment only*. Graduands must register for the ceremony and make an appointment prior to collecting your gowns. You will receive an email with a QR code after you have registered for your collection date and time.
| Date: | 4, 5 & 6 July 2025 (Friday, Saturday & Sunday) |
|---|---|
| Time: | 9.00am – 5.00pm |
| Venue: | School of Social Sciences / College of Integrative Studies Event Lobby |
*If graduands are unable to collect your gowns on campus personally, you may make alternative arrangements:
- Appoint a proxy to collect the gown on your behalf. Please print and fill in this form (Gown Collection Authorisation Form) and present it to the gown vendor during collection.
- Place the order to rent/purchase gown and select delivery. Delivery will be from 7 to 25 July 2025. Delivery charge of $6 will apply.
- For graduands who wish to collect the gown in person, you can contact the gown vendor (admin@nwservices.com.sg) for an alternative collection date from 15 to 25 July 2025 (except 20 July 2025, Sunday), between 10.00am to 5.00pm (excluding lunchtime from 12.00pm to 1.00pm), at Yong Pung How School of Law, Seminar Room 3.09. There will be no gown collection on days of the ceremonies.
Gown Return (for Rented Academic Regalia only)
| Date: | 29 & 30 August 2025 (Friday & Saturday) |
|---|---|
| Time: | 9.00am – 5.00pm |
| Venue: | School of Social Sciences / College of Integrative Studies Event Lobby |
Get Ready for Your Big Day!
Commencement 2025 is around the corner! Follow these steps to register yourself and your guests for the ceremony.
Graduand
Graduands must register for the ceremony.
Check your SMU account for an email in late June/early July from the Registrar’s Office to confirm your eligibility for Commencement 2025. Only those who have officially graduated in the following terms are eligible:
| For Undergraduates: | AY2023-24: Term 3B AY2024-25: Terms 1, 2 & 3A |
|---|---|
| For Postgraduates: | August 2024 – June 2025 |

Guests
Each graduand may invite up to two guests to attend their respective school ceremony. Guest registration must be completed during the graduand's attendance registration.
Key Information:
- Each guest must have a unique email address for registration.
- A confirmation email with a unique QR code will be sent to each guest upon successful registration.
- The QR code is personalised and non-transferable.
- Admittance to the venue is strictly by valid QR code. Guests who cannot present their unique QR code will be denied entry.
Additional Guests:
- Graduands may apply for up to two more admission passes during registration.
- Graduands with double degrees who choose to attend both ceremonies may apply for up to two more admission passes per ceremony.
- Requests are subject to availability and school discretion.
- Successful applicants will be notified via email.
Other Important Notes:
- Guest QR codes will be sent out during the week of 21 July 2025.
- Children below 6 years old will not be allowed into the ceremonies. Proof of age may be required (e.g., birth certificate, passport, or other official ID).
You are viewing this because the primary source was not working well for you.

Professor Lily Kong,
President of SMU
Dear Class of 2025,
Warmest congratulations on reaching this significant milestone!
Today, we celebrate not just your achievements, but the resilience, growth, and spirit that have defined your SMU journey. You have persevered through unprecedented times, embraced challenges, and emerged stronger — and for that, you have every reason to be proud.
Your graduation holds particular significance this year. As SMU marks its 25th anniversary and celebrates our rich legacy of shaping future-ready leaders, you stand among a special cohort whose achievements are forever intertwined with this important chapter in our university’s history. You are, and always will be, part of this proud legacy.
You have also made history in your own right. As the first cohort to receive the SMU Co-Curricular Transcript (CCT), you exemplify the holistic education we champion — one that recognises not only academic excellence, but also leadership, service, global engagement, and real-world experience. These qualities will serve you well in a world that values not just knowledge, but character and adaptability.
In addition, you will benefit from SMU’s new Lifelong Career Support initiative, our commitment to your success beyond graduation. Whether you are embarking on your first role or navigating new opportunities in the years ahead, SMU will remain a steadfast partner in your professional journey.
As you look to the future, stay curious, bold, and be open to new possibilities. Seek out opportunities that challenge and inspire you. Lead with integrity and empathy. Strive not only for success, but also for impact — to make a meaningful difference in the lives of others.
I would also like to express my heartfelt appreciation for your Graduating Class Gift. Your generosity reflects your values and ensures future students can continue to benefit from the transformative education you have experienced at SMU.
Finally, as you step into new beginnings, remember to care for your well-being. You began your university journey during a pandemic, demonstrating extraordinary resilience. As you chart your paths forward, know that balance, fulfilment, and self-care are as important as professional achievements.
Congratulations once again. Wherever life takes you, know that you will always have a home at SMU.
With pride and warmest wishes,
Professor Lily Kong President
Singapore Management University
Overview
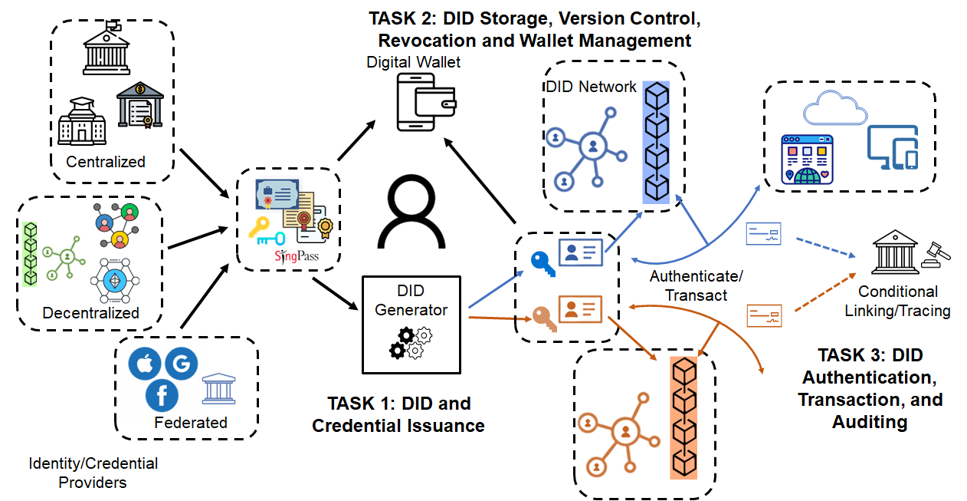
In April 2024, the center was awarded a project entitled “Trusted Decentralized Identities”. The project is funded by the Digital Trust Centre (DTC), a Singapore national Centre at the Nanyang Technological University for coordinating research in trust technology.
A trusted digital identity is an essential component for securely and conveniently accessing services and authorizing transactions in cyberspace. With the rapid development of decentralized technologies and applications, such as distributed ledgers, Web3, and decentralized finance, there is an urging demand for decentralized digital identities (DID), also known as self-sovereign identities, which empower end users to create, own and govern their digital identities and assets in an autonomous, reliable, and privacy-preserving manner.
The overarching goal of this project is to develop and implement a trusted, versatile, reliable and user centric DID framework covering a complete DID lifecycle. Specifically, the project aims to investigate novel techniques for enabling key components and features that are either missing or inadequately addressed in the existing DID proposals.

Limitations of existing DID solutions
- Lack a fully user-centric approach to allow autonomous creation of DIDs with verifiable credentials by leveraging the existing digital credentials and evidences
- Need new solutions to reconcile and balance the privacy and accountability requirements in digital transactions involving self-created DIDs
Technical approach
- A DID-bridging mechanism to port identity attributes from valid sources
- Secure and scalable DID storage, version control, revocation, and wallet management by utilizing blockchain and cryptographic technologies
- Conditional auditing and tracing of anonymous but critical/suspicious transactions by authorized parties
Translation opportunities
- Work closely with collaborators (iSprint, ST Engineering) to meet users/market requirements
- Seek translational funding to develop an operational prototype and conduct extensive user trials

Contact Us
General Contact
Singapore Management University
Administration Building, Level 9
81 Victoria Street
Singapore 188065
Overview
In December 2023, the center was awarded a project entitled “Development of Secured Components & Systems in Emerging Technologies through Hardware & Software Evaluation” (DeSCEmT). The project is funded by the Cyber Security Agency of Singapore (CSA) and National Research Foundation, Singapore (NRF).
In the past decade, mobile devices and Internet of Things (IoT) have become prevalent in our daily lives, both in business and social settings. The applications of such devices have also been growing exponentially due to the development of technologies that support artificial intelligence (AI) and cloud computing. The advances of cloud and mobile computing in the past decade have fundamentally reshaped the computing infrastructure used by individual, business, and government users into a distributed, heterogenous and collaborative system. Modern applications are hence often built as a fusion of data, software, and services from a mixture of stakeholders. Growing with this evolution are the deep-rooted security concerns over a broad spectrum of issues such as leakage of private data, infringement of software copyrights, and corruption of computation results.
This research programme gathers a core team of experts from the Nanyang Technological University (NTU) and the Singapore Management University (SMU) to tackle these security concerns. The SMU team aims to holistically address security challenges in the mobile and cloud computing ecosystem pivoting on the new so-called "confidential computing" techniques featuring hardware-based Trusted Execution Environments (TEEs). The research outcomes are expected to build up the infrastructure and capabilities towards a zero-trust computing domain for industry and government users.

Technical approach
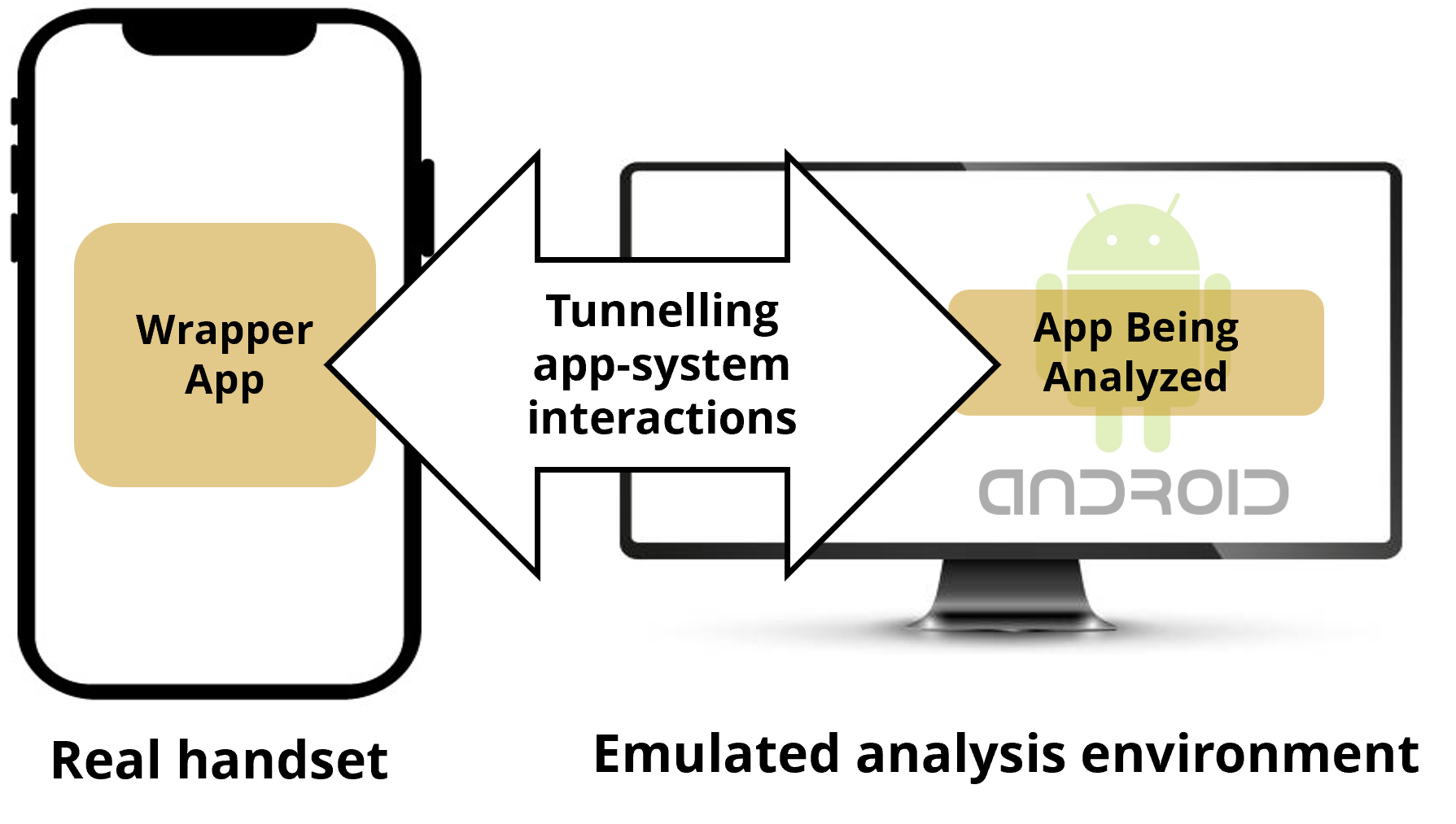
- De-couples the analyzing mechanism from app execution environment
- Runs the analyzing system on powerful emulators
- Uses offloading techniques to mirror app-system interactions to a real handset
Benefits
- Malicious apps can no longer detect the existence of analyzing platform
- Lower performance overhead
- Supports non-pixel phones
Translation opportunities
- Security vetting of mobile apps for government agencies and industry
- Collaborators: DSO, DSTA, GovTech
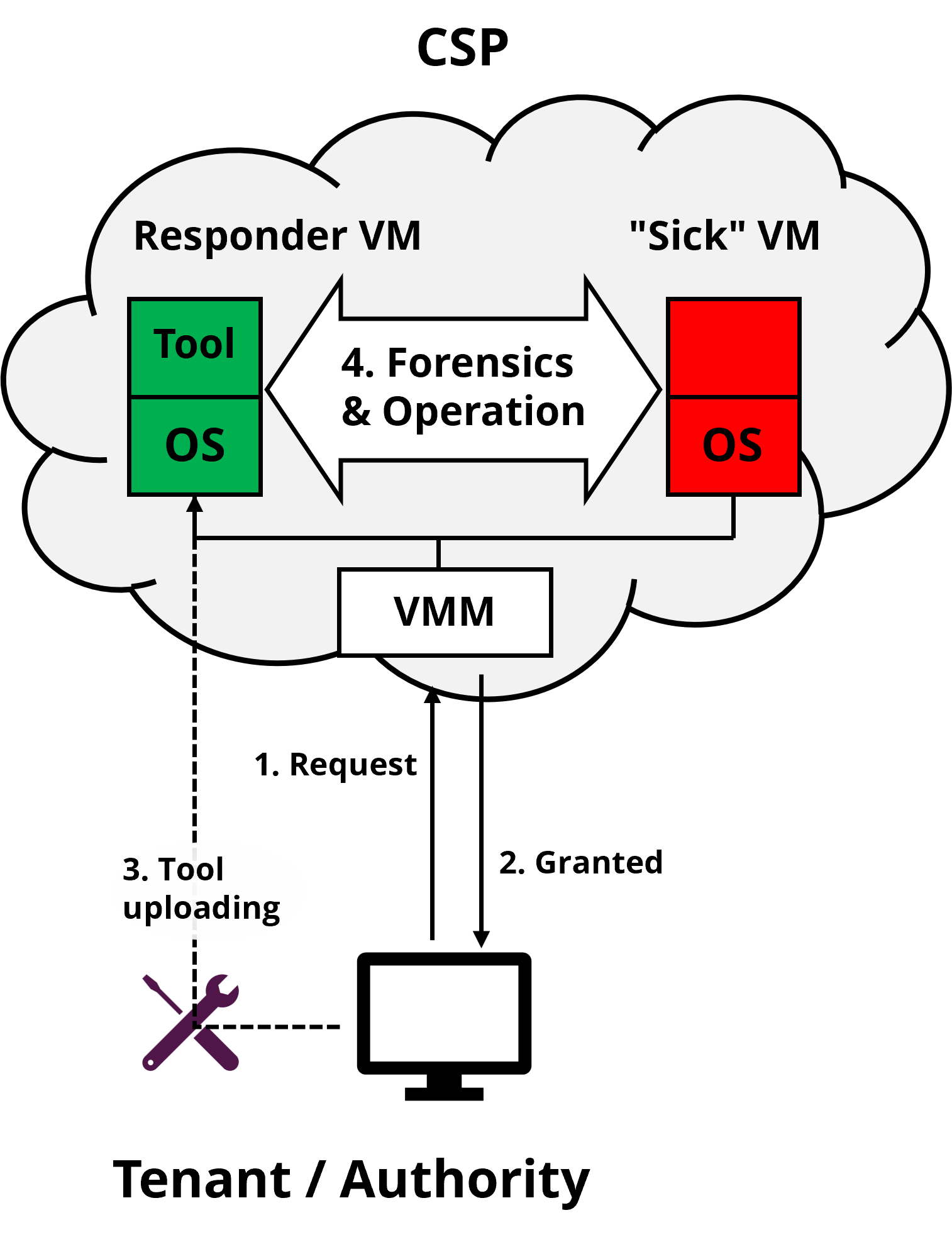
No remedy for misbehaving "sick" VMs due to errors or attacks.
Technical approach
- CSP provides an infrastructure for VMCare. (vm hospital)
- Tenant (or Authority) uses its own tool to introspect and/or rectify the live but misbehaving virtual machine. (vm surgeon)
Impact
- A new cloud service and business model benefit CSP, tenants and authorities.
- Extensible to Android phones to harden user interfaces and analyze malicious apps.
Translation opportunities
- Collaborate with ST Engineering and HTX to conduct pilot tests for feasibility evaluation.
- Apply translation fund to develop an operational prototype and market exploration.
Data breaches are a growing risk [IBM Cost of A Data Breach Report 2023]
- average cost of a data breach in 2023 was USD4.45m, a 15% increase over 3 years
- 82% of breaches involved data stored in the cloud
Limitations of existing cloud data security solutions
- access control is enforced by could service providers and can be by-passed due to backend misconfigurations and leakage of user credentials
- Extensible to Android phones to harden user interfaces and analyze malicious apps.
Technical approach
- access control policies are managed by user organizations and enforced by TEE
- seamlessly integrate TEE and E2E encryption to eliminate top attack vectors
- Support standard/prevalent access control mechanisms to maintain interoperability with popular could platforms
Translation opportunities
- Work closely with collaborators (DSTA, GovTech, HTX, ST EE) to meet users/market requirements
- Seek translational funding to develop an operational prototype and conduct extensive user trials
Why TEE?
Isolating sensitive code and data-in-use in TEE protects them from vulnerabilities in the rest of the app. The usage of TEE is recommended, e.g., in the Monetary Authority of Singapore’s advisory.Problem
- Many applications are not designed for or protected by TEE. Migrating and maintaining an evolving app to properly take advantage of TEEs is complex, time-consuming, and error-prone.
- Bad migration leads to little benefit and even harm.
Technical approach
- Realize a toolchain (Shield-It!, Forge-It!, and Fix-It!) for reengineering & maintenance of evolving applications to benefit from TEE while minimizing costs.
- Investigate SGX and the newly-released Android Virtualization Framework (AVF)
Translation opportunities
- App hardening service for government agencies and industry
- Collaborators: HTX, ST Engineering (project on SGX-protected credit card processing started)

Dive into groundbreaking research at the intersection of security, mobile applications, and cryptography. Explore the latest insights from us, unlocking the secrets of digital protection. Join us on a journey through innovation and discovery, where every click unveils a new layer of technological advancement.